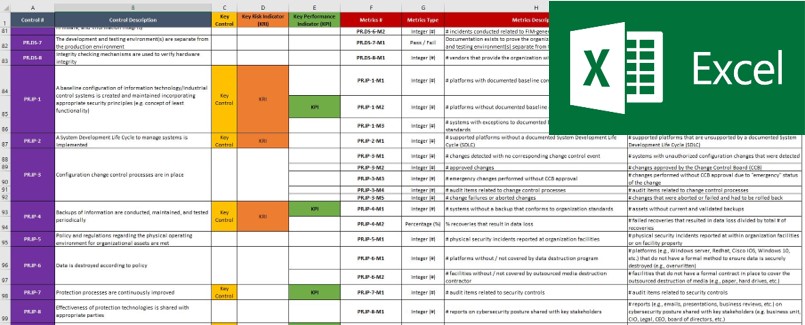
Soc 2 Controls List Excel
We tried to get some great references about SOC 3 Report Example And SOC 2 Controls List for you. It was coming from reputable online resource which we enjoy it.We hope you can find what you need here. We constantly attempt to reveal a picture with high resolution or with perfect images. SOC 3 Report Example And SOC 2 Controls List can be beneficial inspiration for those who seek a picture according specific categories, you can find it in this site. Finally all pictures we've been displayed in this site will inspire you all.

Thank you for visiting.Back To.
I’m using exactly the same card model and wireless lan pci card ew-7128g has had kernel support since 2. You are currently wireleas LQ as a guest. Your card is supported by the rt2x00 module. BTW, if you’re interested, this card uses the rt chipset; the linux driver is developped by the rt2x00 project. Wireless lan pci card ew 7128g driver for mac. “is a website that provides the need to download the Edimax EW 7128G driver and all types of wireless needed, and will be updated according to the development of wireless devices. All drivers that we provide are the latest version for Edimax EW 7128G Driver, Please report if you have problems with the. With the connection speed up to 54Mbps (5 times faster then IEEE802.11b), EW-7128g connects the desktop computer to the wireless network easily. You can also connect to any public wireless hotspot for Internet to retrieve e-mail, surf web sites or use instant messaging. EW-7128g gives you the freedom to join the network. This package contains the files needed for installing the Edimax EW-7128g WLAN Adapter Driver. If it has been installed, updating (overwrite-installing) may fix problems, add new functions, or expand existing ones. Even though other OSes might be compatible as well, we do not recommend applying this release on platforms other than the ones.
The AICPA guide Reporting on Controls at a Service Organization Relevant to Security. Illustrative Type 2 SOC 2SM Report: Reporting on the Security and Availability of a. Requests against the users' authorized roles in access control lists.